Introduction
The other day, I see a the post of Jai Minton in the blog of Crowdstrike, talking about how the team of CrowdStrike found a intrusion that start with the use of a seemgly empty SFX archive.
After read the post, which I recommend you to do the same, I was curious about how it worked and I wanted to be able to replicate it, hence this post is based on how to perform an attack of this type.
I will soon post other related entries on how to improve the attack, for now let’s start with something simple.
What we need
For this first tutorial, I only use a Windows 10 VM (with RDP active) and WinRAR.
Steps
The idea is backdoring an machine where we have admin privileges with a expose RDP, following the attack chain that Jai let us in his post.
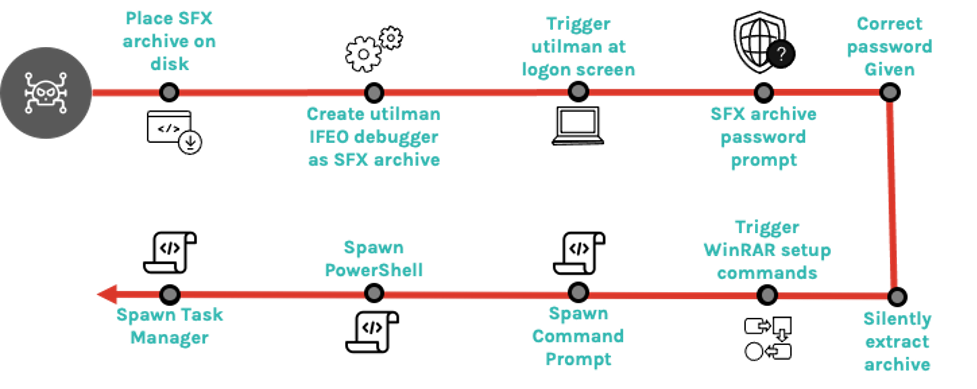
We need Winrar instaled in the machine. Create a empty file and with right click and select the option Add to archive…
Note: the file name will appear when we launch or sfx, so for more opsec, consider giving it a name such as “Windows Update” or something like that.
After that:
-
Select in the GUI of Winrar, General > Archiving options > Create SFX archive (see how our file change the extension for .exe).
-
Set a password.
-
Go to the tab Advanced > SFX Options
3.1 Setup > Run after extraction. Add in this dialog box the following;
powershell.exe cmd.exe taskmgr.exe3.2 Modes > Silent Mode > Hide all
3.3 Update > Update Mode > Extract and replace files
3.3 Update > Overwrite mode > Skip existing files
-
Press Ok, and create the file. Check that all work correctly.
-
Now we need to create a “persistence” using utilman.exe with the debugger option linked to our sfx file. For that we need to save the sfx file in the Windows 10 Victim and the path.
Note: Disable Windows Defender, the option “Debugger” in the registry is detected.
Command to automate the process. (thanks Jai)
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\utilman.exe" /v "debugger" /d "[REDACTED PathToSFXArchive]" /f
Now we can close our session and try to connect to the machine via RDP. When we connect we just click in the “Easy to access” options and our sfx will be launched. Just put the password and now you have a NT AUTHORITY\SYSTEM session.
Demo
Thanks! See you next time in another post.
